International Journal of Advancements in Technology
Open Access
ISSN: 0976-4860
ISSN: 0976-4860
Research Article - (2017) Volume 8, Issue 2
Data and network security is one among the foremost necessary factors in today’s business world. In recent, businesses and firms like financial institutions, law firms, schools, health sectors, telecommunications, mining and a number of government agencies want a strategic security technique of managing its data. Organizations managing bigger monetary information, bio-data and alternative relevant info are losing its valuable information or data at rest, in usage or in motion to unauthorized parties or competitors as a result of activities of hackers. Organizations are losing millions of dollars as a result of unprotected data that gets into the hands of malicious persons. Data protection in an organization has become vital in today’s business. In order to possess secure information, this information should be protected in order that although malicious persons get access to the info, it becomes wealthless and useless to them. Advanced Encryption Standard (AES), could be a scientific discipline rule that may be used for secured data and communication in an organization, it uses same key that's isobilateral key for transmission additionally as reception. The AES rule is capable of using cryptographic keys of 128, 192, and 256 bits, this paper implement AES block cipher of 256-bits and 256-bit key size, developed with C# as a front-end client machine and MS SQL used for the database as a back-end machine.
<Keywords: Cryptography, AES algorithm, Decryption, Encryption, Cipher, 256-bit-key
The scrambling of plaintext delivers a safe and nice significance for secured data and communication. Use of scientific discipline algorithms is completed for the aim of security in varied applications like secured optical disk content, ATM, etc. Secured data and communication in an organization is one in all the foremost necessary things in present day business and its requirement is rapidly increasing [1-3].
With the introduction of LAN, WAN, MAN and internet technology in recent years, the computer network communication is exposed to unwanted people giving them access to pose different kinds of attacks on personal and organizational data in a network environment [4].
Every individual desires, their information to be secured and privacy should be maintained. This demand is consummated by the employment of cryptography. Numerous security systems are needed to guard a shared information in an organization. The paper focuses on cryptography to secure the info of an organization in motion within its network, at rest, and in usage to unauthorized parties.
The science of writing or transforming the meaning of data into secret data to prevent people from reading is generally termed as Cryptography [5]. The history of the earliest use of cryptography was documented close to 1900 B.C., associate Egyptian academician was ready to generate and much used a non-standard symbols in writing messages. Cryptography became thus common throughout the missives wartime era wherever battle plans and communication ways were predominate within the earlier period. Once the utilization of laptop and alternative device were introduced into the communication system, there was the necessity for a correct management of data keep on these devices. In information, communications and networking, cryptography is important once human action over a transmission medium, particularly the un-trusted medium, significantly the net [5].
The encrypted knowledge is named as ciphertext. At the receiver part, solely those that have a secret key can decipher the message into plain text to obtaining the initial knowledge [6]. Generally encrypted messages are often lessened by cryptography, which is thought as code breaking. Cryptography is often classified into 2 varieties symmetrickey systems and Asymmetric-key systems [3]. In symmetric-key secret writing systems sender and receiver of the message, create use of the identical key, this distinctive secret is used for secret writing also as coding of the message [3]. In all cases as illustrated in Figure 1, the original unencrypted data is referred to as plaintext (X). It is encrypted into ciphertext (Y), which will in turn (usually) be decrypted into usable plaintext with the same key (K) used for encryption.
Cryptography does not only protect data from theft or alteration, but can also be used for user authentication in most application [5].
Description of AES algorithm
On January two, 1997, government agency National Institute of Standards and Technology (NIST) declared the initiation of an attempt to develop the AES and created a proper concern algorithms on September twelve, 1997 [7]. AES is a block cipher which is also known as Rijndael algorithm and it was developed by Joan Daemen and Vincent Rijmen. The algorithm can efficiently be executed on a variety of computer processors and hardware’s. The robust AES development process and its complex internal structures ensures very secure algorithm and has no known weaknesses. In accordance with the AES requirements, Rijndael’s key length can be 128, 192 or 256-bits. Rijndael algorithm is made up of variable block size that can also be 128, 192, or 256-bits. This implies that, a Rijndael algorithm with key sizes of 128, 192 and 256-bits provides approximately [8]. AES is one of the most up-to-date out of the four current algorithms approved for federal United States within the US [9].
AES internal structure
AES composition and building blocks was designed based on standard known as a substitution-transformation arrangement with fixed block size of 128 bits, and a key size of 128, 192, or 256 bits and has a high-speed in both software and hardware.
Unlike its predecessor DES, AES is not based on Feistel network [5]. The principle of AES design is known as a substitution-permutation network, which is the combination of both substitution and permutation. AES operates on a 4 × 4 column-major order matrix of bytes, known as the state. However, some versions of Rijndael have a larger block size and have additional columns in the state. Generally, AES calculations are done in a special finite field called Galois Fields, which allows mathematical operations to scramble data easily and effectively [7,10]. There are numerous rounds within the AES encryption development. Each operational round consists of more than a few processing steps, each one containing four similar but different stages, including the one that depends on the encryption key itself. The various stages are ByteSub, ShiftRows, MixColumn and addRoundkey.
Encryption
The preliminary key is added to the input value at the beginning stage in the encryption mode, which is called a preliminary round. Several repetitions follows immediately after the initial round with a slightly modification of the final. The following operation are perform in every one round respectively.
Subbytes conversion
The SubBytes convention stage is a non-linear byte replacement, where each state byte is operated independently. This is achieved through an S-box. S-box is a pre-calculated replacement table which holds 256 numbers (from 0 - 255) and their matching resulting value. The SubBytes step has each byte in ai,j in the state matrix swapped with a SubByte bi,j by means of an 8 bits substitution box, known as Rijndael S-box.
However, the SybBytes transform algorithm is based on Galois Field Inverse operation GF (28) known to have excellent non-linearity properties. The use of Galois Field is to prevent attacks based on simple algebraic properties. The S-box is created by merging the inverse function with an invertible affine transformation. The S-box is selected in order to prevent any fixed operational networks, thus, ai,j ≠ bi,j. For additional knowledge in S-box table calculations refers to [11]. S-box table as shown in Table 1.
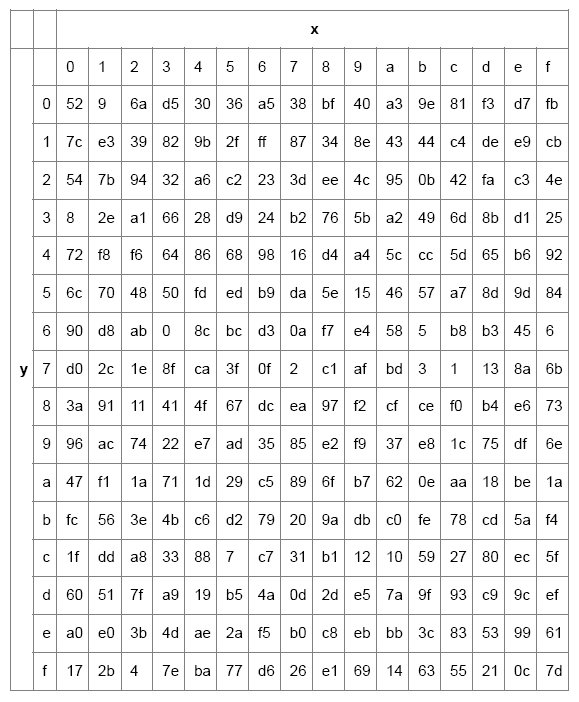
Table 1: S-box table.
Shift Rows: In Shift Rows transformation stage, each row of the state is intermittently left shifted above diverse offsets. Row 0 remain in position, whiles row 1,2 and 3 are shifted one byte, two bytes and three bytes to the left respectively [12].
Mix Column: From the Mix Column operations, there is a transposition of linear transformation made to join the 4-byte in each column as shown in Figure 2. The task of this step is to take 4-byte as input and outputs 4-byte, where every input bytes have an effect on all the output 4-byte. Each column is transformed using fixed matrix operations; this is composed of multiplication and addition of the entries as illustrated in Figure 2. Addition is simply XOR. Multiplication is modulo irreducible polynomial [13,14]. In the MixColumn process, each column is treated as a polynomial over GF (28) and is then multiplied modulo with a fixed matrix polynomial c(x) multiplies every column, thus,
C (x) = 3x3 + x2 + x + 2
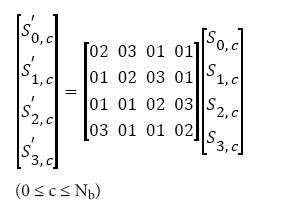
Figure 2: Overall structure of AES algorithm (Source: http://crypto.stackexchange.com/questions/8043/aes-addroundkey).
addRoundkey: For every round in the AddRoundKey step, a subkey is generated from the main key by means of Rijndael’s key schedule. The subkey is combined with the state, and that notwithstanding each subkey is the same size as the state (Figure 3). The subkey is inserted by combining every byte in the state with it related byte in the subkey by means of bitwise XOR [15].
Related works
A FPGA-based implementation of the Advanced Encryption Standard (AES) algorithm was proposed by [15]. The design employs an iterative looping technique with block and a 128 bits key size S-box table implementation. The research concluded that low complexity architecture and easily achieves low latency as well as high throughput 1054 Mbit/sec for encryption and 615 Mbit/sec for decryption was achieved. An implementation of high speed AES algorithm with Key Length of 256 Bits based on FPGA is presented was proposed by [16] to advance the security of data in motion. [17] proposed FPGA-based implementation of the Advanced Encryption Standard (AES) algorithm in UART Module. The design employs an iterative looping technique with block and a 128 bits key size S-box table implementation. A throughput 1054Mbit/sec for encryption and 615 Mbit/sec for decryption was achieved in their research. A proposed FPGA-based implementation of the Advanced Encryption Standard (AES) algorithm was also presented by [14]. The design employs an iterative looping technique with block and a 128 bits key size S-box table implementation. Their design was executed using APEX20KC FPGA on Altera which is based on great performance design. In their paper, a low latency and the throughput attained a value of 1054Mbit/sec for encryption and 615 Mbit/sec for decryption [14]. An implementation of AES encryption and decryption standard AES-128 was proposed by [18]. All the transformations of each secret writing Associate in nursing decoding are simulated victimization an unvarying style approach so as to reduce the hardware consumption. Their paper proposed that their methodology will create it a really lowcomplex design, particularly in saving the hardware resource in implementing the AES InverseSub Bytes module and Inverse combine columns module. Because the S - box is enforced by look-up-table during this style, the chip space and power will still be optimized. The new combine Column transformation improves the performance of the inverse cipher and additionally reduces the quality of the system that supports the inverse cipher. As a result this transformation has comparatively low relevant diffusion power. This allows for scaling of the design towards vulnerable moveable and cost-sensitive communications devices in client and military applications [18]. Proposed implementation of the 128 bit AES normal on a Field Programmable Gate Array (FPGA) for significant level of security similarly as quicker time interval in order that it will be used for secured communication of ATM, optical disc content similarly as for secured storage of confidential company documents, government documents [3].
The above discussions show that an implementation of AES algorithm with 128 key length can be enhanced with a 256 bits key length to provide a well secured data [9], hence this paper focuses on the implementation of the AES algorithm with a 256 bits key length to prevent data loss in an organization.
Tools and methods
Microsoft Visual Studio 2012 (C#) was employed to develop the face, where system users (client) will diagrammatically communication to the server via a web browser. The rear finish (database) was developed with Microsoft Structured command language (MSSQL) server 2008. A Wireshark hacking tool was used for testing the encrypted data.
Design concept: Figure 4, shows the pictorial view of the proposed layout for the implementation of the AES algorithm with 256 bits key length for organizational data protection.
A web application with login details of client as shown in Figure 5 was developed to collect raw data in plaintext.
Five different data was collect from the front end for testing purpose. The data transmission from the client machine to server was done in two section A and B. In section A the data was transmitted raw (no encryption) over vulnerable medium to the server. The Wireshark hacking tool was used to intercept the data packets in transmission and the raw format of the packets are displayed by the network packet analyzer in a plain text as illustrated in Figure 6.
Same client with ID 700701 data was transmitting under section B, which fully encrypted with AES 256 bits block cipher before transmission. Again the Wireshark hacking tool was used to intercept the packets in transit but the network packet analyzer displayed scrambled letters which has no meaning to the hacker as shown in Figure 7.
Results for unencrypted data in the server
Figure 8 shows the stationary data saved in the server which clearly indicates the system did not implement any form of encryption which means all the data saved are in plaintext under section (A) category. It is very risky and extremely dangerous to transmit sensitive information without proper measure to protect or shield it. This implies that any hacker getting access to the save can easily get hold of the organization data in its raw (plaintext) format.
Results for encrypted data in the server
Figure 9 shows the saved data of an organization that transferred data in an encrypted. The input data, the intercepted data and the data saved in the server are different. The input data has been scuttled by the AES 256 bits block cipher algorithm hence, the saved data in the server has been completely protected by the application.
The tests conducted indicate a high level security for data in transit and stationary. The data protection using AES is to provide optimized data security to classified and non-classified data. The test conducted for all the five client using the developed web application indicated a successful data protection. When encryption algorithm was use to encrypt the data, it was realized that data in transit, data saved in the server are highly protected and major data losses. The results also results of the data seen in the server shows that even if a hacker hacks or intercepts the data through a hacking tool or social engineering, the data will be meaningless the him/her. This research will solve problem of organizations losing their sensitive data to unauthorized persons, a 256 bits key length offers more security to data both at rest and in transit [3].
Organizations with virtual offices at remote location require this form of application to enable their remote workstations to communicate securely with the server. Since the ciphertext was encrypted with AES 256-bit and key size of 256 bits offers a better and a more secured that as compared with [3,14,15,18,19] that employed 128 key length, anyone who want to crack an AES with 256 key length will requires 2256 possible keys to be able to use brute force to decrypt a character of the key. An average throughput 1054 Mbit/sec for encryption and 615 Mbit/sec for decryption was realized from the test analysis.
Due to the high level security capabilities provided by AES with 256 bits key length, we recommended to organization such as school, banks, microfinance and churches, that seeks to do a secure business transaction both online or on corporate network infrastructure to protect the data of its clients, staff, partners and supplier with AES with 256 bits key length algorithm.