Journal of Information Technology & Software Engineering
Open Access
ISSN: 2165- 7866
ISSN: 2165- 7866
Short Communication - (2023)Volume 13, Issue 3
The article presents a network of SREXPES8–2 with two round functions, which uses a single algorithm for encryption and decryption of sequential blocks of parts. Cryptography, or cryptology (from Antiquated Greek: κρυτπός, romanized: kryptós "covered up, secret"; and γράφειν graphein "to compose" or λογία-logia, "study", respectively), is the training and investigation of strategies for secure correspondence within the sight of ill-disposed behavior. All the more by and large, cryptography is tied in with developing and examining conventions that keep outsiders or the general population from perusing private messages. Present day cryptography exists at the convergence of the disciplines of math, software engineering, data security, electrical designing, advanced signal handling, physical science and others. Center ideas connected with data security (information classification, information trustworthiness, validation, and non-disavowal) are additionally fundamental to cryptography. Commonsense uses of cryptography incorporate electronic business, chip based installment cards, computerized monetary standards, PC passwords, and military correspondences. Cryptography preceding the advanced age was really inseparable from encryption, changing over decipherable data (plaintext) to muddled garbage text (ciphertext), which must be perused by turning around the interaction (decoding). The shipper of a scrambled (coded) message shares the unscrambling (unraveling) strategy just with planned beneficiaries to block access from enemies. The cryptography writing frequently utilizes the names "Alice" (or "A") for the source, "Sway" (or "B") for the planned beneficiary, and "Eve" (or "E") for the listening in adversary. Since the advancement of rotor figure machines in The Second Great War and the approach of PCs in The Second Great War, cryptography techniques have become progressively complicated and their applications more shifted.
Feystel network; Lai-Massey scheme; Encryption; Decryption; Round keys; Round functions
The article presents a network of SREXPES8-2 with two round functions, which uses a single algorithm for encryption and decryption of sequential blocks of parts. Cryptography, or cryptology (from Antiquated Greek: Κρυπτός, romanized: Kryptós "covered up, secret"; and γράφειν graphein, "to compose", or-λογία-logia, "study", respectively), is the training and investigation of strategies for secure correspondence within the sight of ill-disposed behavior. All the more by and large, cryptography is tied in with developing and examining conventions that keep outsiders or the General population from perusing private messages. Present day cryptography exists at the convergence of the disciplines of math, software engineering, data security, electrical designing, advanced signal handling, physical science, and others. Center ideas connected with data security (information classification, information trustworthiness, validation, and non-disavowal) are additionally fundamental to cryptography. Commonsense uses of cryptography incorporate electronic business, chip-based installment cards, computerized monetary standards, PC passwords, and military correspondences.
Cryptography preceding the advanced age was really inseparable from encryption, changing over decipherable data (plaintext) to muddled garbage text (ciphertext), which must be perused by turning around the interaction (decoding). The shipper of a scrambled (coded) message shares the unscrambling (unraveling) strategy just with planned beneficiaries to block access from enemies. The cryptography writing frequently utilizes the names "Alice" (or "A") for the source, "Sway" (or "B") for the planned beneficiary, and "Eve" (or "E") for the listening in adversary [6]. Since the advancement of rotor figure machines in the second great war and the approach of PCs in the second great war, cryptography techniques have become progressively complicated and their applications more shifted.
The PES block encryption algorithm was developed in 1990 and is based on the Lay-Messi scheme. In 1991, the authors redesigned this block encryption algorithm and named it IDEA [1,2]. In these block encryption algorithms, round keys are multiplied by the module on the part blocks 216+1, added by the module 216 and in the MA reflection, the module 216, XOR add operations are used that is the number of operations is limited. However, a single algorithm is used for encryption and decryption. The IDEA NXT block encryption algorithm is based on the extended lay-Messi scheme developed by P. Junod, et al. Later, the IDEA NXT algorithm came to be known as FOX [3].
Currently, block encryption algorithms using a single algorithm for encryption and decryption are widely used. Examples of such block encryption algorithms are block encryption algorithms based on the Feystel network. In the Feystel network, the substitution actions are reflected in the round function, and the round functions do not depend on the network structure. It is also possible to take one sided, that is non-reverse, functions as round functions. Even with the structure of the PES block encryption algorithm and the extended Lay-Messi scheme, the creation of a network using a single algorithm for encryption and decryption using a round function instead of the MA reflection in the algorithm is a topical issue. Based on the above, in this paper, the structure of the PES block encryption algorithm and the extended Lay-Messi scheme, the eight-part block, extended by XOR using the XOR operation, consists of two round functions, the block length is 32 bits, the block length is 256 bits, the block length is 128 bits. The SREXPES8-2 (successfully replaced extended by operation XOR PES) network in the form of a series of algebraic operations (z0, z0, z1, z1, z2, z2, z3, z3) in which the block blocks are used to create block encryption algorithms with bits (Figure 1) [4-6].
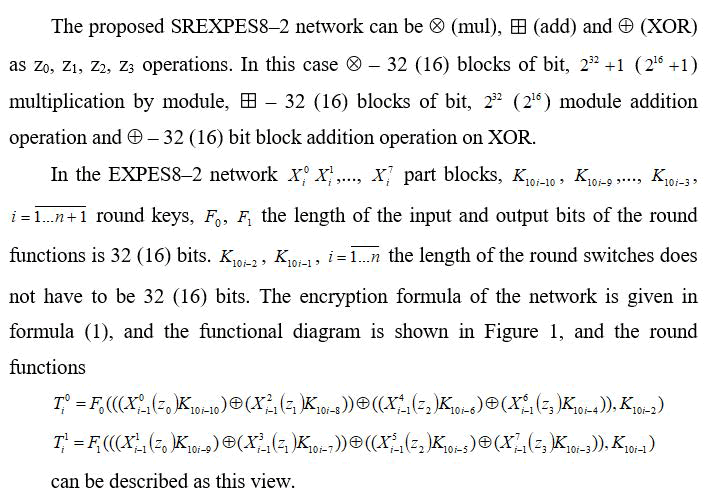
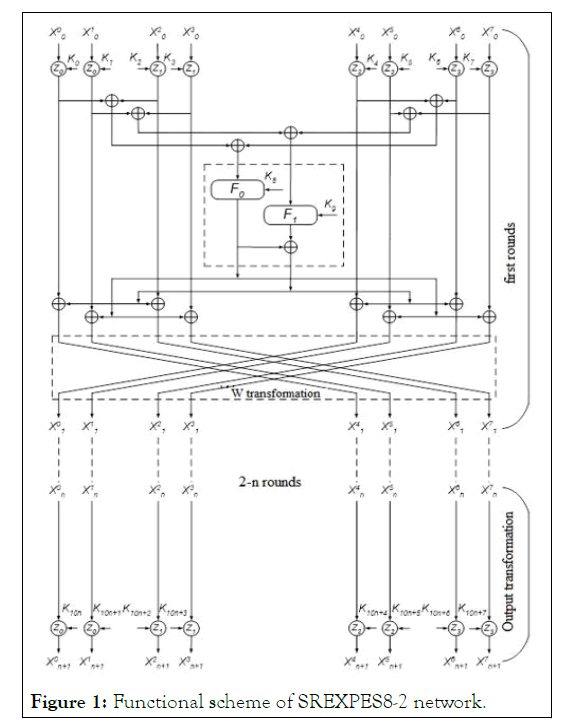
Figure 1: Functional scheme of SREXPES8-2 network.

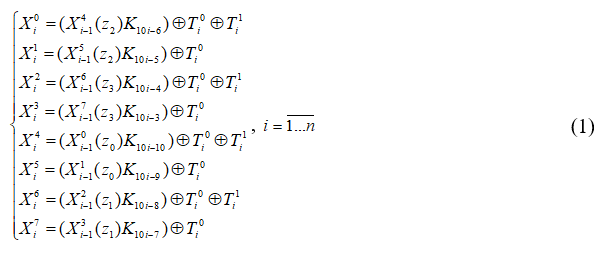

Calculations exchange their places:
In the round n-, SREXPES8-2 network, there are 10 round switches in each round and 8 round switches in the final reflection that is the total number of round switches 10n+8. In encryption, the encryption round keys are generated from the algorithm key Ki c according to one rule 10n+8.
one rule 10n+8. 10n+8 times decryption round keys are created based on encryption round keys. Encryption uses the encryption round key instead of 1st figure and formulas Ki and the decryption round key Kic is used in encryption, that is one network is used for encryption and decryption Kid, only the order of the keys changes. The n–round SREXPES8-2 network connects the first, second, and n-round decryption keys to the encryption round keys as follows:
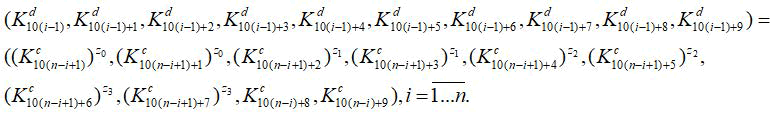
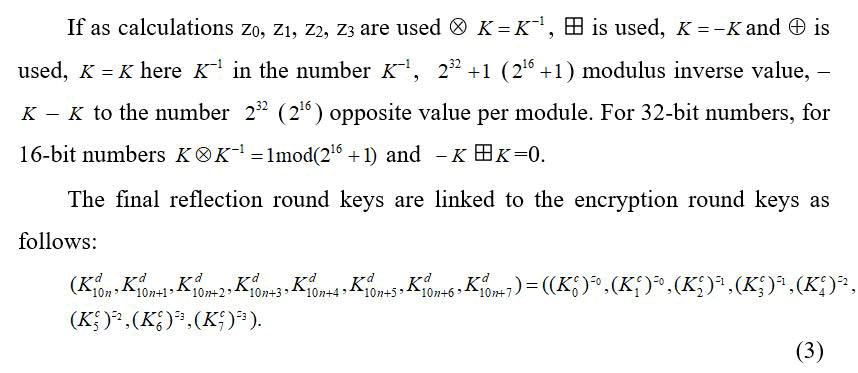
The main advantage of the proposed SREXPES8-2 network is that it involves a round function, uses a single algorithm for encryption and decryption, and algebraic operations are variable. As a network round function, it is possible to obtain reflections that are widely used in block encryption algorithms, as well as one-way, that is, non-existent reflections. As actions z0, z1, z2, z3 add, mul, chorus actions, in the vision of (z0, z0, z1, z1, z2, z2, z3, z3) in the way of 34=81 can be choosen that is, all possible options are equal to 81, and the network has four options.
By selecting operations F0, F1 in 81 ways and options in eight ways, it is possible to build 648 block encryption algorithms based on the SREXPES8-2 network, whose round functions do not change. Block encryption algorithms based on the SREXPES8-2 network facilitate the development of hardware and software by using a single algorithm for encryption and decryption in the network.
Citation: Tuychiyev G, Jumakulov A. Extended srexpes8-2 Network Using Symmetrically Interchangeable XOR Operations. J Inform Tech Softw Eng. 13:332.
Received: 19-Sep-2022, Manuscript No. JITSE-22-19258; Editor assigned: 21-Sep-2022, Pre QC No. JITSE-22-19258(PQ); Reviewed: 05-Oct-2022, QC No. JITSE-22-19258; Revised: 10-May-2023, Manuscript No. JITSE-22-19258(R); Published: 17-May-2023 , DOI: 10.35248/2165-7866.23.13.332
Copyright: © 2023 Jumakulov A, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution and reproduction in any medium, provided the original author and source are credited.