International Journal of Advancements in Technology
Open Access
ISSN: 0976-4860
ISSN: 0976-4860
Research Article - (2023)Volume 14, Issue 5
Heinous offenses against women have forced us to undertake many precautionary measures and put on a large array of ideas so that to provide security systems to women via their phones. Here we present, an android application for women safety, this app can be activated by just normal movements like shaking, as situation demands. Our main agenda is to create a model that removes the financial and physical complexities in GPS, since it is a satellite based service alongside being available anytime anywhere. GPS system can come handy to extract data which contains parameters like latitude, longitude along with the time details, etc. There exists no prior financial investment for its usage. ’Google maps’ is a popular service for this purpose. Mobile phone catches hold of location which communicates with the help of General Packet Radio Service (GPRS), being one of the superior modes as far as tracking concerned.
Android; GPS; URL; Registered contacts; Text messages; PMIS
In today’s world, safety for women is one of the most important issues that should have been a fundamental, concept for all societies’ centuries ago. Not accepting fundamental rights to safety, personal choices, lifestyle to practice, physical empowerment are quite regular issues but have been not managed to be removed even in today.
The lazy legal proceedings regarding the horrific crime case of ‘Nirbhaya’ exposed the dire need to stop these crimes being committed.
Survey of the study
Today ladies are enjoying a very important role in each field. Even nowadays ladies have achieved prime positions in jobs and society; nonetheless they are facing issues like physical harassment and sex crime. So, it is essential to develop a system to produce security to ladies.
Because of increased participation of women in public sphere, the chances of assaults against them increase too [1]. It is encouraging that the social patriarchal mindset is getting challenged to quite an extent, if not to the full extent that was anticipated. The same mentality prevents women from working outside the home, limiting their roles only up to domestic purpose. In this essay, the author aimed to provide a solution to protect women from these scenarios by creating a tool that looked like a standard belt. This design includes a buzzer (for sound purposes), zapper, GPS (for location purposes). Women can utilize the device with the emergency button when they feel uneasy. High voltage shocks from zapper circuits provide the attacker a non-deadly jolt [2-4].
Violence towards women should not be ignored on any grounds of difference of identities. Worldwide, one among three girls has endured sex based violence, and similarly than 15 million women elderly 15-19 instances have continued rape. As women and girls lose their help structures and homes, they are positioned in insecure environment and in new locations, their risk of gender grounded violence, consisting of sexual violence, intimate mate violence and infant abuse will increase day via way of means of day. Areas of public spaces, public transport, etc. were the house of girl’s nimrods. In this paper, the writer proposed a device correspond of android operation, predominant tool, and movable digital digicam. Android operation makes use of Phone GPS or GPS of the primary tool to come across the sufferer within side of crucial scenario there had been dire need of the exigency button. The digital digicam can be delivered through the print can be captured and it will be transferred to the garçon with ensure the statistics security; Main tool is likewise connected with manually working in pepper spray [5].
This research is based on a health maintenance app which uses android as its OS. They have developed an application called EKG android app that provides users with visualization of the electrocardiogram. Background data logging capability, sorted data upload to Wi-Fi cloud to monitor record for future analysis of the person, internet of things and cloud technology developed from this idea. IOIO microcontrollers, signal processing, communication protocols, secure and efficient large file transfer mechanisms, database management systems, and the cloud. Visualization of his ECG waves in android app. ECG waves was recorded through data transmitted from the IOIO microcontroller's sensor through bluetooth. Method of loading ECG data over Android app: A large amount of data received by the IOIO microcontroller is combined into a binary file containing all received data and this file is stored on the mobile's SD card. The scalability and performance of this feature are enhanced. The upload service: Using an FTPES-secured server, the service transfers files from a device's SD card to a private, centralized cloud. The file transfer protocol is used to move the file over the internet protocol. Using fill table and file stream technology in Microsoft SQL server 2012, unstructured data is being able to be stored without causing any database latency. Because the cloud supports both multiple users and multiple devices, ECG data can be sent simultaneously from multiple devices to the server. Security and compression of files. The clinical information is put away in a paired configuration which would be encoded and transferred to the cloud in a solid way utilizing FTPES convention. It is specially modeled with intention of compressed memory and quicker byte pulsing in the cloud. The author of this paper proposes a method that makes use of an IOIO-OTG microcontroller to track a patient's ECG wave from any location in the world. An android application has been developed for easy access to monitor ECG. Using a USB cable, the android phone is connected to the IOIO-OTG microcontroller [6].
Developed a security device to defend ladies from vulnerable activity and lonely traveling on the road. Mistreatment IoT supported the fingerprint security methodology [7]. During this system the GPS pursuit and electronic communication system play a vital role. Once ladies’ area unit progressing to travel somewhere for long distances in the dark the GPS used as a GPRS location whereas travel within the cab would be accessible and at the same time her location is going to be in real time sent to their relative for his or her rescue. The most purpose of planning such a project is that we are going to create tiny, handy instrumentality that might be unbroken during a purse. This instrumentality is going to be having a panic switch and as before long because the panic switch is switched on, the location coordinates provided by the GPS to the emergency. The panic switch is extremely tiny and it will simply handle with safe and secure from others which is a straight forward thanks to does that. Whereas press that switch associate degree emergency/alert message regarding the victim location gets shared to the police room and can be told through the benefit of the web site.
This paper describes unique feature of sending messages to desired contacts, for which there is facility of storing number in form of list. An icon is specifically allotted for giving that alert [8]. The coordinates of location might be constantly changing, messages are continuously being sent unless the ‘panic’ mode is switched off [9].
This device uses the alarm technique. It will trigger when the bluetooth connection is disconnected and the GPS application is used to track the location of the child who’s wearing this device. The child detector device has 2 main units which are for parents and children. The child's units function as a transmitter that transmits a GPS signal, while the parent’s units will receive the signal which will determine the position and distance of their child using their own smartphone. This device uses the alarm technique. It will trigger when the bluetooth connection is disconnected and the GPS application is used to track the location of the child who’s wearing this device. The child detector device has 2 main units which are for parents and children. The child's units function as a transmitter.
In case bluetooth is disconnected this will get triggered. GPS service is used for catching location. The detector equipment contains 2 functioning units one for parents and other for the operator. The user units’ prime function is to precede a GPS signal, while the module belonging to parents will contain the packets which will in turn plot the coordinates on map [10].
Wi-Fi module is the key factor which makes the whole system wireless. Since then, GSM module does not need direct wired connection with any microcontroller [11]. The main disadvantage of the Above mentioned mobile applications is that when a women is in trouble, there can be times when it will not be possible to take the phone out of the bag, open the application and press the button. Moreover, a study suggested that although carrying phone gives sense of security as well as talking on a mobile phone has been found to reduce individuals’ awareness of their surroundings and slow reactions to unexpected events.
Quite an issue of other contemporary apps is that when there is an unfortunate situation, manually operating a phone will not be thoughtful act. Further, analysis suggests that time needed to respond has been quite high since the user was operating it for other purposes.
System requirements
• Active Internet connectivity is needed. (public networks
should be avoided in general).
• Minimum 1.5 GHz processor.
• 20 MB free space.
Required permissions
• Internet access.
• Read/write external storage.
• Read/write internal storage.
• Location enabled.
• SMS permission.
Module of operating
Android being based on Linux operating system is also open source. Storage with regards to android is not an issue since it is expandable by the help of secondary memory products. Devices operated by android have wired connections to hardware components, like motion capturing cameras, movement sensors, etc. Android smartphones also notify coordinates of points where Wi-Fi can be easily accessed, as the user change position, continuously leaving traces of data containing points with reference to maps. Further this help to plot points on map system. Home automation is also possible by using various extensions of Android, ranging to devices like Geysers, Garage doors etc. [12].
Firebase (data base)
In our following presented android application, we used ‘Firebase’ website which is a google extension. Basic structure of the feature is carried by google and is compatible, for apps of all domains, sizes, and versions as far as possible. It helped immensely in development of this app and provides varied options like handling data arrays, and analysis reports without needing to do it manually so we could focus on the needs of users. For login and sign-up, authenticating through firebase is required during development. All the details regarding clients, multimedia memory etc., is stored in fire-store, which can also be called as brain of fire base [13].
Sensor
Many android using products like smartphones already come up with a huge array of sensors like accelerometer, gyroscope, etc. Selection of sensors like the accelerometer, magnetometer, or gyroscope is done solely on device; in return they put up data for software, taking the note of various device positions in all and around three axes. By combining all data acquired we can perform desired operations. Any high intensity output like bell ring can be aligned with given signal. To prevent output when not needed, that option can be disabled as well.
Various facilities and feature structure were individually created and then assembled after.
• Identity confirmation: Here the user can enroll itself with
the desired password. The right confirmed user can use the
program and exercise its functions. It takes hold of the
user actions like organizing phone numbers from user’s
phonebook for fast-track use.
• Editing information: The user can have a straight
access here. It protects confidential information in the file
manager. The path of the files is sent to the local server
which is accessible later. List of emergency contacts is editable
by user if needed.
• Signalling facility: The user will be notified by SMS to contacts
stored in list. As soon as the alert function are alerted, program
views current coordinates by help of pre-installed GPS service
within phones, then the users get the current address using the
same eceived by SMS earlier. By taking note of their registry
numbers, tracking the device will get easier.
• Main shield module: As name suggests this is main module
and maintain sync between various services like clearing
memory, retrieving message and Eliminate contacts, making
main screen inaccessible. The moment shield gets switched on,
arrays of data kept within memory drives gets cut out entirely
simultaneously baking up all the contacts and messages in
internal memory section.
• Fake call: In a case of dire emergency, when the lady is
surrounded by potential danger or sensing so, it is necessary to
get of situation. The fake call feature can be used to arrange a
reason by ringing the phone with number and other info
displaying on it.
• Multimedia support: Since the app focuses on self-defence,
hence appropriate links for videos for self-defence from YouTube
platform are also included. In order to watch those, YouTube UI
is also included as well. Rather one can access YouTube can be
accessed as well. Moreover, other facilities are also included like
recorded voice messages using in-built microphone.
• Database module: This module contains all the data stored in
the background. The emergency contact numbers are also
registered in this module.
Algorithm
For first we open the app, a window will appear so that one can register and make an account on it. Full name will be asked followed by email address, phone number, and lastly password which is not supposed to be disclosed. Further up ahead interface of app comes first, where a detailed GPS location with latitude and longitude of the person will be shown on a map.
Below it, there will be two options will be seen, first is that of getting the values of coordinates and the one below is of forwarding the location via SMS. At left side of screen, a list will appear where various options will be visible. We shall go through them one by one [14,15].
• Add contacts: Here, user can create a separate speed dial
by importing/adding contacts from their phonebook. Those
contacts can also be called as mediators.
• Videos: This feature comprises of YouTube videos
regarding self-defense and various other types of threats
in public space etc.
• Emergency helpline: The toll-free number issued by
government is being accessed on your dial space.
• Siren system: It is a unique feature available here. A loud
siren sound is played on loop hence will help in dragging
the attention of surrounding public.
• Record audio: This also one of our multimedia facilities
added. This feature helps in recording the audio and storing
in phone’s storage space which might be very useful in future
use.
Algorithm techniques
• Decision tree algorithm: Decision tree algorithmic rule
is a subset of supervised learning algorithms, helping to
predict value using earlier records.
• KNN algorithmic rule: Used where huge data is there.
Operates by constructing various comparisons (Table 1).
| App | Notification | YouTube facility | Fake call | Cost |
|---|---|---|---|---|
| She safe | Inconsistent | No | No | Free |
| Life 360 | Yes | No | No | Free |
| Hollaback | Screenshot | No | No | Paid |
| VithU | Yes | No | No | Free |
| Fight back | Vibration only | No | No | Paid |
| Raksha | Vibration only | No | Buzzer | Paid |
| Be safe | Yes | No | No | Free |
| Street safe | Yes | No | No | Paid |
| Safety pin | Yes | No | No | Free |
Table 1: Comparative study with existing techniques.
At last, on front screen itself at lower right corner a bell like icon will be visible, it comes at handy when the user gets a sense of danger, let’s say in all alone in a taxi at dark nights. Then by giving a jerk to phone three times the user will convey its position in form of coordinates to all the stored contacts besides contacting authorities (Figures 1-9) [16-18].
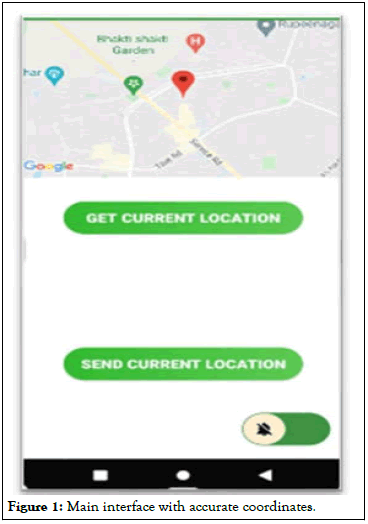
Figure 1: Main interface with accurate coordinates.
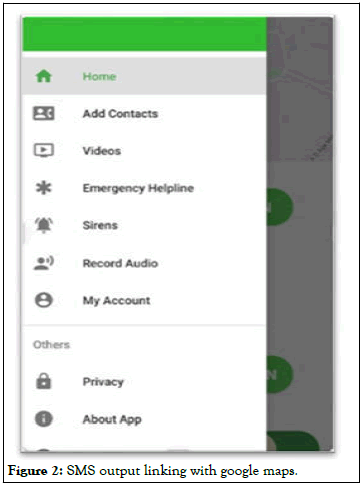
Figure 2: SMS output linking with google maps.
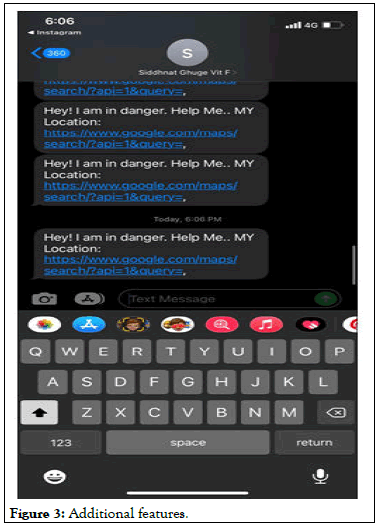
Figure 3: Additional features.
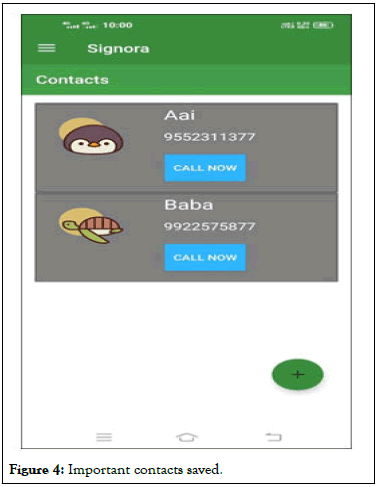
Figure 4: Important contacts saved.
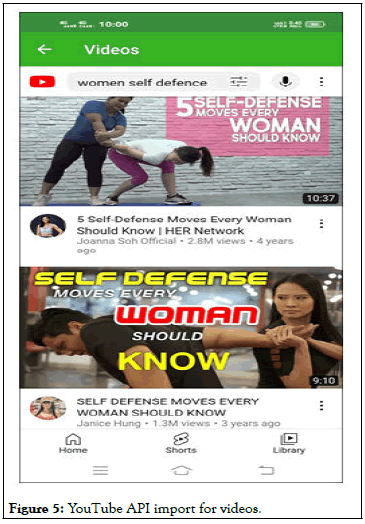
Figure 5: YouTube API import for videos.
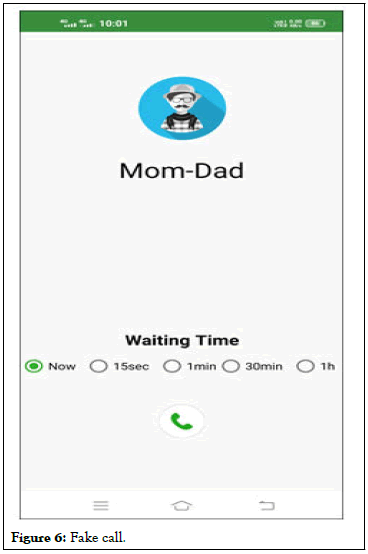
Figure 6: Fake call.

Figure 7: Important helplines.

Figure 8: Siren.
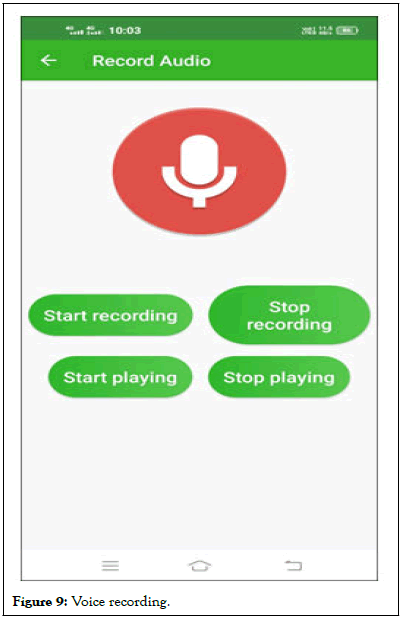
Figure 9: Voice recording.
Here is the “safety ensurement for women app” which might a path breaking tool for women safety. For example, in night time travelling alone in a cab/taxi one can update its location. Hence application consists required parameters necessary for an ideal application in this domain.
• Extra security features like biometric; retina scan etc., can be
added.
• Implementing the application without the use of internet.
• Providing emergency balance in case of zero balance
situations.
• By tapping the feet twice or thrice we will try to make live
video call to the registered mobile number.
• Furthermore, recording can be extended to up to marking
sounds as concerning by users itself.
Citation: Janokar S, Gaikwad V, Ghuge S, Ghorpade S, Gholap S, Ghuge P, et al. (2023) Handy App for Safety against Violence. J Geogr Nat Disasters. 14:255.
Received: 22-Apr-2023, Manuscript No. IJOAT-23-23696; Editor assigned: 24-Apr-2023, Pre QC No. IJOAT-23-23696 (PQ); Reviewed: 08-May-2023, QC No. IJOAT-23-23696; Revised: 22-Jun-2023, Manuscript No. IJOAT-23-23696 (R); Published: 29-Jun-2023 , DOI: 10.35248/0976-4860.23.14.255
Copyright: © 2023 Janokar S, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.